An undertanding of routing protocol is very important to understand the attacks, perform network traffic inspection.
Routers are the devices connected to the different networks at the same time, they are able to forward IP datagrams from one network to another.

most of us have our own router at home to provide us with the internet, routers can be the gate of the internet world, also routing protocols are used to determine the best path to reach the network, the behave like a postman who tries to use the shortest path to deliver a letter.
A router inspects the destination address of every incoming packet and then forwards it through one of its interfaces .
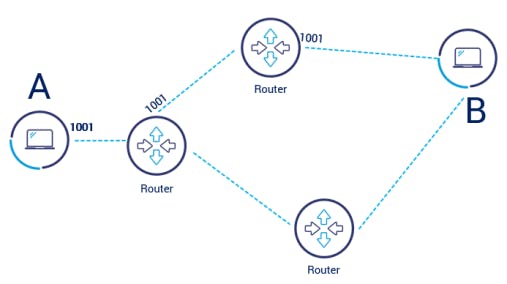
Understanding how the router works are very important to the pentester because it will make it easier for him to analyze the network.
Routing Table:
To choose the right forwarding interface, a router performs a lookup in the routing table, where finds an IP to interface binding.
the table can also contain an entry with the default address (0.0.0.0). the entry is used when the router receives a packet whose destination is unknown.
How to check the routing table :
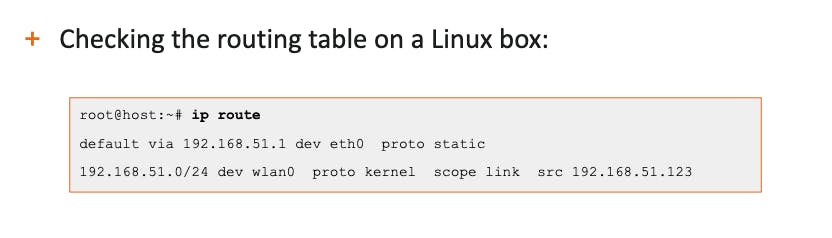
the routing table are not only keep in the routers, every host stores its own table, you can check them by using the following commands :
IP route
on Linux
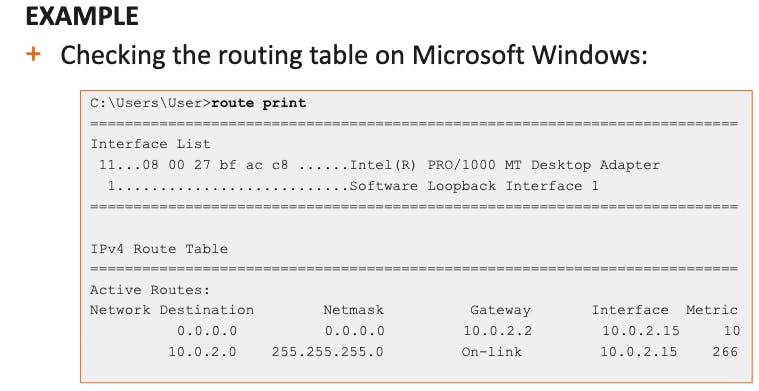
route print
on windows
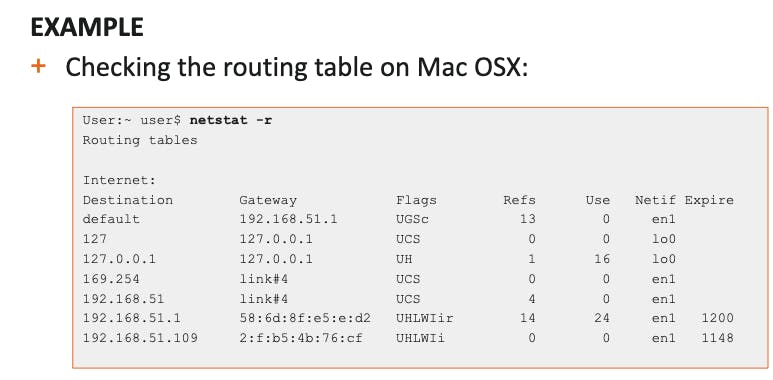
netstat -r
on OSX
In the next article, I will write about link Device protocols.
Written by : Mohamed Abdalla Ibrahim
PMP | CISM | ITIL | CEH | Azure Architect | Azure Security Engineer | IBM Cybersecurity Analyst In the next article, I will write about link Device protocols.
Written by : Mohamed Abdalla Ibrahim
PMP | CISM | ITIL | CEH | Azure Architect | Azure Security Engineer | IBM Cybersecurity Analyst

