CYBER SECURITY (Penetration Testing Prerequisites) 1.8 Firewall and Network defense
-There are many different appliances on the market that a system administrator can use to protect the network. -These devices use different techniques and work on different layers to perform access control, attack detection, and prevention.
So, How Does this support my pentesting career?
- Evading firewalls
- Advanced stealth scanning
- Filtering evasion
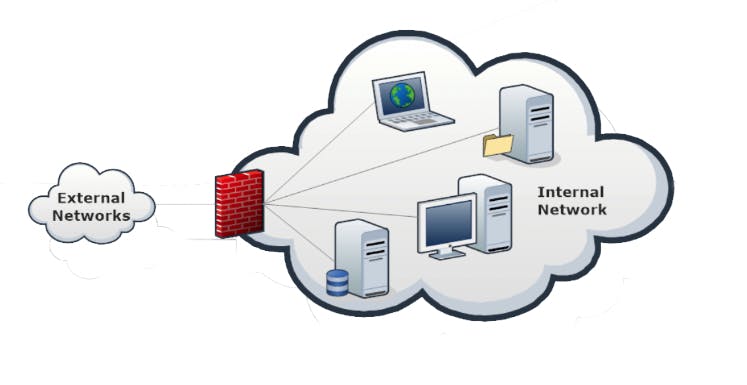 -Firewalls are specialized software modules running on a computer or a dedicated network device.
-Firewalls are specialized software modules running on a computer or a dedicated network device.
-They serve to filter packets coming in and out of the network.
*Firewalls help system administrators and desktop users to control the access to network resources and services.
*A firewall can work on different layers of the OSI model, thus providing different features and protections.
*It is imperative that you understand how firewalls work and what kind of threats they prevent.
*Many people believe that firewalls and antiviruses are all they need to stay secure, in the following slides, you will see why this idea is wrong.
Packet Filtering Firewalls :
The most basic feature of a firewall is packet filtering.
With packet filtering, an administrator can create rules which will filter packets according to certain characteristics like:
-Source IP address -Destination IP address -Protocol -Source port -Destination Port
-> Packet filters run on home DSL routers as well as high-end enterprise routers and are the cornerstone of network defense.
- Packet filters inspect the header of every packet to choose how to treat the packet. The more common actions are:
Allow: allow the packet to pass.
Drop: drops the packet without any diagnostic message to the packet source host.
Deny: do not let the packet pass, but notify the source host.
Example: Inspecting the Header of a packet does not give you any information on the actual packet content.
- In a company, network administrators configure a corporate firewall to allow web browsing from the internal network. They do that by allowing TCP traffic to have 80 or 443 as destination ports. What happens if an internal machine tries to connect via SSH to a server listening on port 80?
Packet filtering VS Application attacks :
Let's now look at a typical example where packet inspection does not stop a hacker from exploiting a server.
A company hosts a web server. The firewall will allow all incoming traffic from the Internet and direct it to port 80 of the webserver.
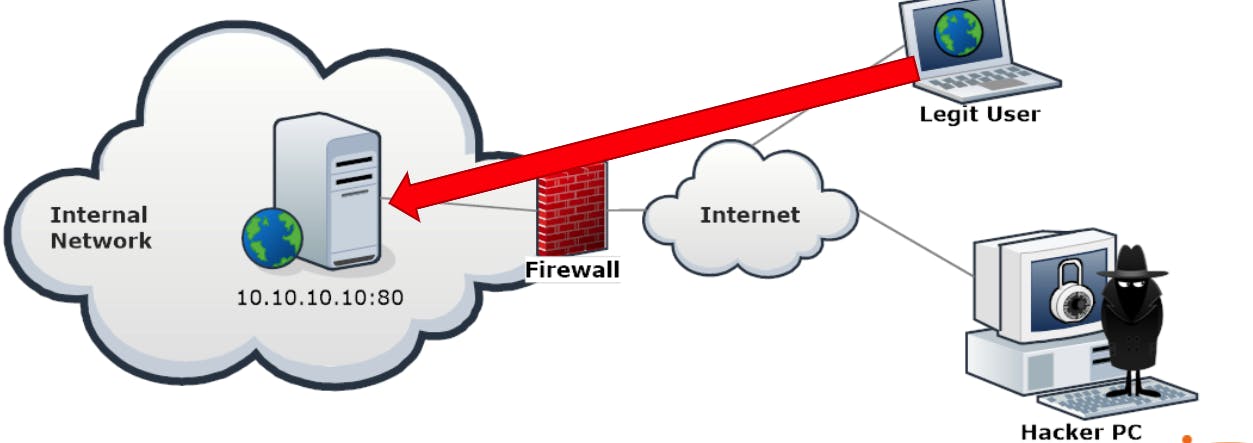
In the same way, application exploits will go through, because the firewall cannot see the difference between web browsing and web application exploits.
The firewall can only filter traffic by using IP addresses, ports, and protocols. Any kind of application-layer traffic will pass, even hackers' exploits.
+A n application layer exploit could be an XSS, a buffer overflow, a SQL injection, and much, much more.
- Packet filtering is not enough to stop layer 7 attacks.
- Let's take a look at another scenario.
okay let me give you an example :
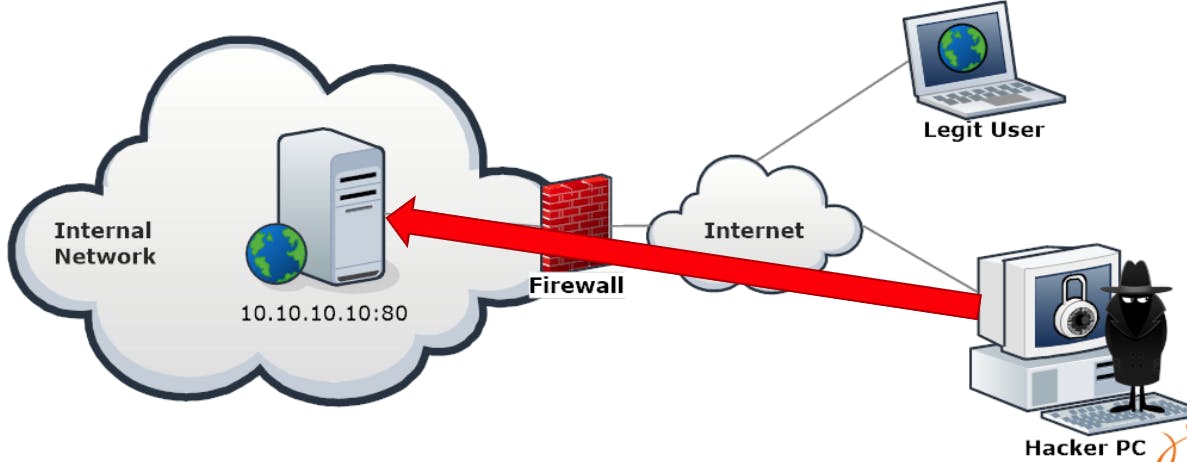
A hacker manages to exploit a workstation in a company network and wants to install a Trojan horse to remotely manage that machine.
The Trojan, by default, can be configured to accept connections on port 123 TCP or UDP or to connect back to the hacker's machine on port 123 TCP or UDP.
A typical firewall configuration rule is to let HTTP traffic (TCP.dst = 80) pass, so internal workstations can browse the Internet. The remaining traffic is dropped.
-> So What happens to the trojan horse?
- The hacker cannot connect to the infected machine, as there are no rules to allow traffic coming to port 123.
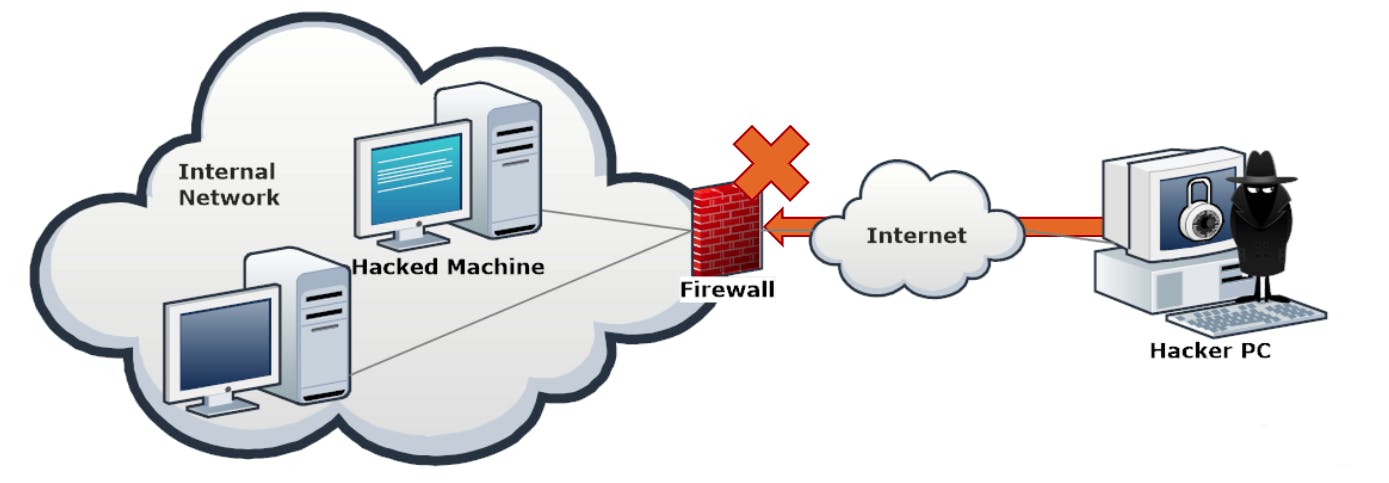
- Similarly, the firewall will deny the traffic from the infected machine to the hacker's PC.
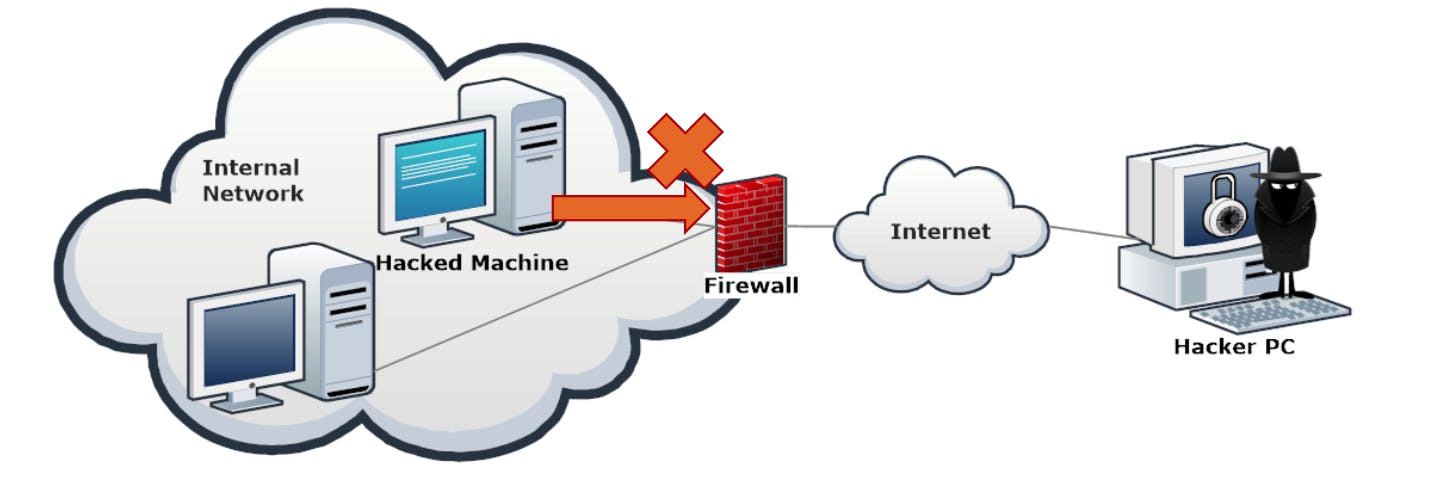
What happens if the hacker, who is smart and knows all the well-known ports by heart configures the Trojan to connect back to his or her machine on port 80?
- The Firewall will allow the connection.
Application layers firewalls :
- Application-level firewalls work by checking all the OSI7 layers. +They provide more comprehensive protection because they inspect the actual content of a packet, not just its headers. For example: -Drop any peer-to-peer application packet. -Prevent users from visiting a site.
-> Level 7 firewalls are indeed able to understand most of the application layer protocols in use nowadays. Organizations use them not only to protect their network from hackers but also to filter unwanted traffic.
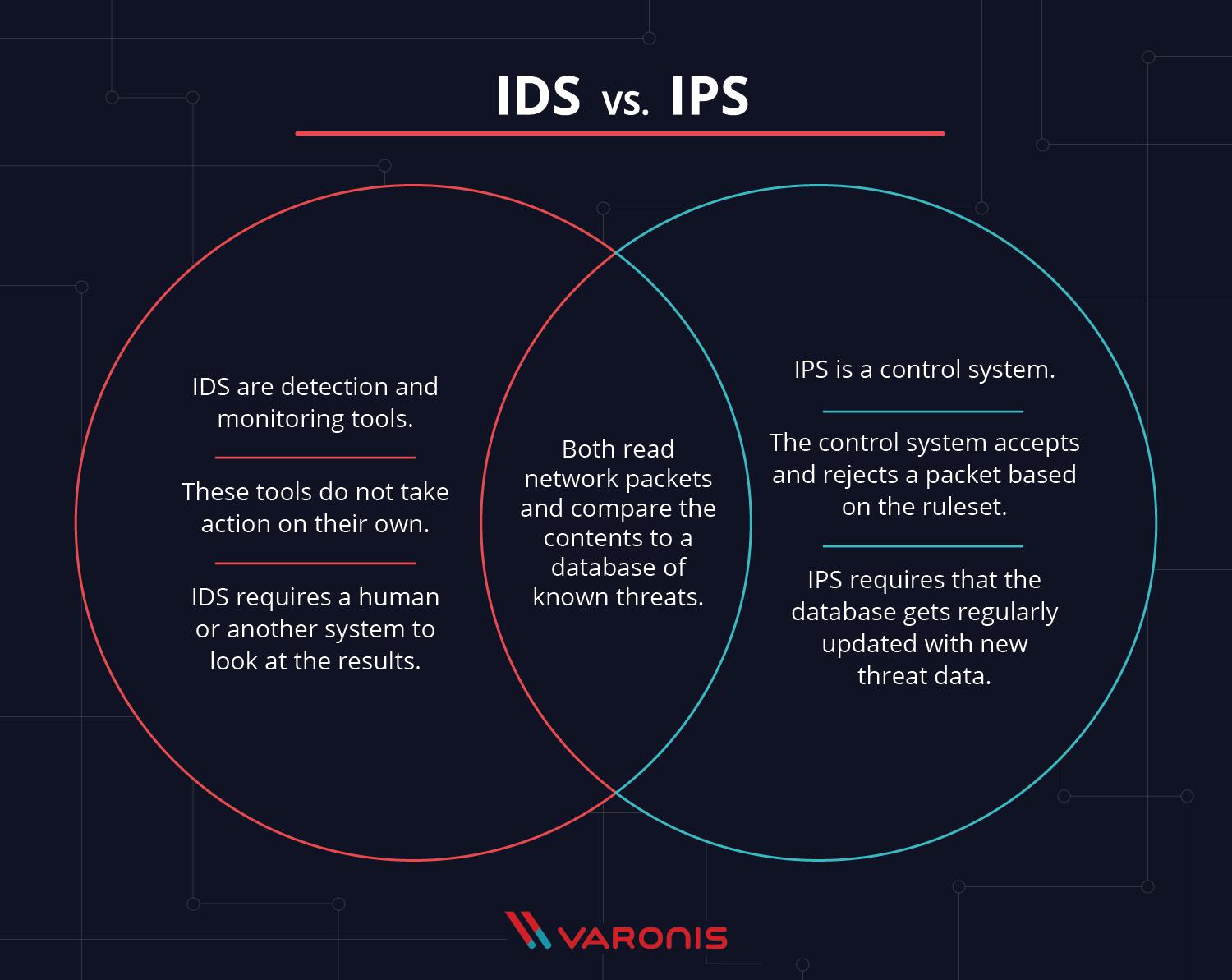
IDS VS IPS
Refrences :
amazon.com/Firewall-Fundamentals-Wes-Noonan..
linuxsecurity.com/resource_files/intrusion_..
In the next article, I will write about DNS.
Written by : Mohamed Abdalla Ibrahim
PMP | CISM | ITIL | CEH | Azure Architect | Azure Security Engineer | IBM Cybersecurity Analyst

