Keeping Your Azure Cloud Safe: Best Practices for Securing Resources (2 .Secure management ports)
Welcome back to my blog! In this article, we'll be discussing the importance of secure management ports in Azure. With the increasing number of cyberattacks targeting cloud environments, it's more important than ever to ensure that your Azure resources are protected from unauthorized access. One of the key aspects of securing Azure resources is ensuring that the management ports used to access and manage your resources are properly secured. In this article, we'll explore what management ports are, why they need to be secured, and the best practices for securing them in Azure. Specifically, we will cover the following topics:
Internet-facing virtual machines should be protected with network security groups
Management ports should be closed on your virtual machines
Management ports of virtual machines should be protected with just-in-time network access control

Internet-facing virtual machines should be protected with network security groups
Internet-facing virtual machines should be protected by network security groups. In the world of cybersecurity, it's always important to have multiple layers of defense. One way to secure your internet-facing virtual machines (VMs) in Azure is by using network security groups (NSGs). An NSG is a firewall-like mechanism that contains a list of Access Control List (ACL) rules that dictate which network traffic is allowed or denied to your VM. This way, you can restrict access to your VM from other instances in or outside the same subnet, effectively protecting your VM from potential threats.
To keep your machine as secure as possible, it's crucial to restrict its access to the internet and enable an NSG on the subnet. High-severity VMs are considered internet-facing, so it's even more crucial to have an NSG enabled for these VMs. By implementing an NSG, you'll have another layer of security to protect your internet-facing VMs from cyber attacks.
To protect a virtual machine with a Network Security Group:
1. Select a VM from
2. Assign the relevant NSG to the NIC or subnet for the VM you're protecting:
a. To assign the NSG to the VM's subnet (recommended):
i. In the Networking page, select the 'Virtual network/subnet'.
ii. Open the "Subnets" menu.
iii. Select the subnet where your VM is deployed.
iv. Select the Network Security Group to assign to the subnet and click "Save".
b. To assign the NSG to the NIC:
i. In the Networking page, select the network interface that's associated with the selected VM.
ii. In the Network interfaces page, select the 'Network security group' menu item.
iii. Click 'Edit' at the top of the page.
iv. Follow the on-screen instructions and select the Network Security Group to assign to this NIC.
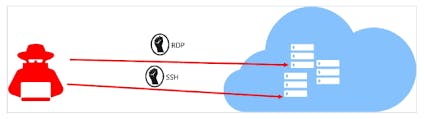
Management ports should be closed on your virtual machines
Management ports should be closed on your virtual machines. As you strive to keep your virtual infrastructure secure, it's important to pay attention to open management ports. Open remote management ports can expose your VMs to a high level of risk from Internet-based attacks. These types of attacks often attempt to brute force credentials to gain administrative access to the machine.
To reduce the risk of such attacks, it's best to close any remote management ports that are not needed. This will limit the attack surface of your VMs and prevent cyber criminals from gaining unauthorized access to your machine. By closing the management ports on your virtual machines, you'll be taking a critical step in securing your virtual infrastructure.
To ensure the management ports on your virtual machines are secure, I recommend that you edit the inbound rules of some of your virtual machines to restrict access to specific source ranges.
Here are the steps to restrict access to your virtual machines:
Select a VM to restrict access to.
In the 'Networking' blade, click on each of the rules that allow management ports (for example, RDP-3389, WINRM-5985, SSH-22).
Either change the 'Action' property to 'Deny', or, improve the rule by applying a less permissive range of source IP ranges.
Click 'Save'.
By following these steps, you can effectively close the management ports on your virtual machines and reduce the risk of Internet-based attacks.
Management ports of virtual machines should be protected with just-in-time network access control
Just-in-time (JIT) network access control is an effective measure in securing your virtual machines. With Defender for Cloud, you can lock down inbound traffic to your Azure VMs by demand. This means that access to management ports is granted only when it's needed, reducing the attack surface for internet-based attacks such as brute-force attacks. By implementing JIT network access control, you can ensure that your virtual machines are protected and secure against potential threats.
To enable just-in-time VM access:
On the "JIT VM access configuration" page, define the ports for which the just-in-time VM access will be applicable.
To add additional ports, select the "Add" button on the top left, or select an existing port and edit it.
On the "Add port configuration" pane, enter the required parameters.
Select "Save".
In conclusion, securing management ports on your virtual machines is a critical aspect of protecting your Azure resources. By restricting access to management ports through network security groups and just-in-time network access control, you reduce the risk of internet-based attacks and protect your resources from potential threats. By following the steps outlined in this article, you can ensure that your virtual machines are secure and protected against potential risks. Remember, security should always be a top priority in your cloud infrastructure, and taking these measures will help to ensure the protection of your valuable data and resources.