Keeping Your Azure Cloud Safe: Best Practices for Securing Resources (1 .MFA)
As more and more businesses move to the cloud, the need for robust security measures becomes increasingly important. Azure is a powerful cloud platform that offers a wide range of resources and services, but it also requires a thorough understanding of security best practices to keep your data and infrastructure safe. In this article, I will explore some of the key security considerations for Azure resources and provide practical tips for securing your cloud environment. From identity and access management to network security, I will cover the essentials to help you protect your Azure resources from potential threats."
It's always a good idea to have a broad understanding of the Azure platform and its security features before implementing any security measure.
MFA
Multi-Factor Authentication (MFA) is a critical security measure that adds an extra layer of protection to your Azure account. By requiring users to provide two or more forms of authentication, MFA makes it much more difficult for unauthorized individuals to gain access to your resources. In this article, I will focus on the importance of enabling MFA for accounts with the owner and writing permissions on Azure subscriptions and resources. I will also provide step-by-step instructions for implementing MFA in your Azure environment, so you can take action to secure your resources and protect your business from cyber threats."
1-MFA should be enabled on accounts with the Owner permissions & write permissions on subscriptions
Multi-Factor Authentication (MFA) should be enabled for all subscription accounts with owner permissions to prevent a breach of accounts or resources.
To enable MFA using conditional access you must have an Azure AD Premium license and have AD tenant admin permissions.
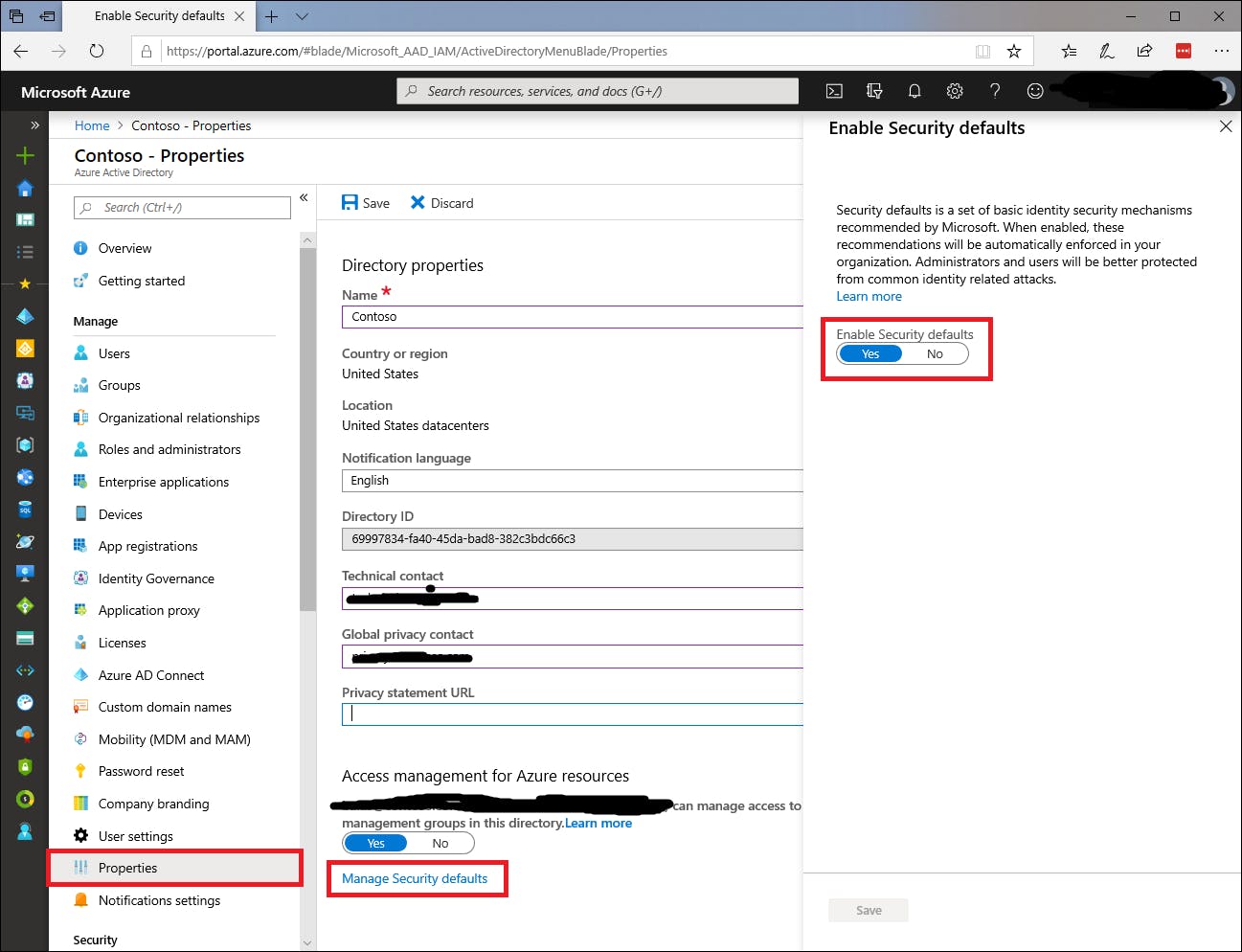
To enable MFA security defaults in Azure Active Directory (included in Azure AD free):
1. Sign in to the Azure AD - Properties page as a security administrator, Conditional Access administrator, or global administrator.
2. From the bottom of the page, select Manage security defaults.
3. Set Enable security defaults to Yes.
4. Select Save.
Note:
- It can take up to 12 hours for the change to be reflected in Defender for Cloud.
- To enable MFA using conditional access you must have an Azure AD Premium license and have AD tenant admin permissions
2-Accounts with the Owner permissions & write permissions on Azure resources should be MFA enabled
If you only use passwords to authenticate your users, you are leaving an attack vector open.
By enabling Multi-Factor Authentication (MFA), you provide better security for your accounts, while still allowing your users to authenticate to almost any application.
Multi-factor authentication is a process by which users are prompted, during the sign-in process, for an additional form of identification.
To prevent breaches and attacks, I recommend you to enable MFA for all accounts that have to write permissions on Azure resources.
More details and frequently asked questions are available here: Manage multi-factor authentication (MFA) enforcement on your subscriptions
Security defaults (included in Azure AD free)
To enable MFA security defaults in Azure Active Directory:
Sign in to the Azure AD - Properties page as a Security Administrator, Conditional Access administrator, or Global administrator.
From the bottom of the page, select Manage security defaults.
Set Enable security defaults to Yes.
Select Save.
Per-user assignment (included in Microsoft 365 Business, E3, or E5 plans)
To enable MFA per-user assignment:
Sign in to the Azure AD - All users page as a Global administrator.
From the top menu, select Per-user MFA.
Find the user(s) you want to enable for per-user MFA and check the box next to the name(s) of the user(s).
On the right-hand side, under quick steps, choose Enable.
Confirm your selection in the pop-up window that opens.
Conditional access (CA) policy (included in Azure AD Premium plans)
To enable MFA using conditional access you must have an Azure AD Premium license:
Sign in to the Azure AD – Conditional Access page as a Conditional Access administrator, or Global administrator.
In the Conditional Access page, add the list of users to a policy (create a policy if one doesn't exist).
For your conditional access policy, ensure the following:
In the Access controls section, choose Grant and ensure Require multi-factor authentication is enabled.
In the Cloud Apps or actions section's 'Include' tab, check that Microsoft Azure Management or All apps are selected. In the 'Exclude' tab, check that it is not excluded.
Select Save.
In conclusion, enabling MFA for accounts with owner permissions on subscriptions is a critical step in securing your Azure resources.
By requiring two or more forms of authentication, MFA adds an extra layer of protection to your subscription, making it much more difficult for unauthorized individuals to gain access. I have provided step-by-step instructions for implementing MFA in your Azure environment, and I encourage you to take action to secure your resources and protect your business from cyber threats. Remember, this is just one aspect of securing Azure resources, and there are other security measures to consider such as securing and managing ports. In the next article, I will discuss this topic in more detail and provide tips for keeping your Azure environment secure