CYBER SECURITY (Penetration Testing Prerequisites) 1.2 Cryptography and VPNs
Before you started your pentesting career you should understand how information is transmitted over computer networks, choose the right protocol, knowing how to protect the traffic. Thus you must know what is the purpose of cryptography and VPNs
Clear-Text : Clear text is the opposite of ciphertext, which means transmitting data over the network without any kind of encryption. this lets an attacker eavesdrop on the communication as well as perform any other malicious action aka (change data, capture data,..) which effected the integrity and confidentiality, this kind of attack, we can call it man on the middle attack.
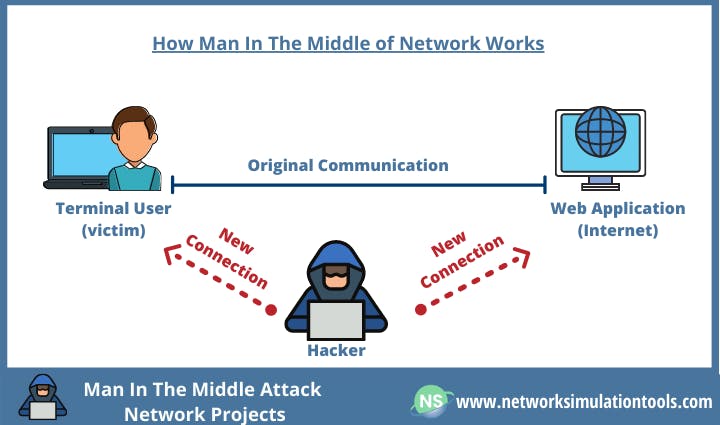
it's an Idea close to when we were young we had many phone sets at home, and during any phone call, someone pick up one of those phone sets and hears my phone conversation.
Because of the nature of the clear text, we should use it only in a trusted network, on the other hand, Cryptographic protocols Transform (Encrypt) the information transmitted to protected communication, its main goal is to prevent eavesdropping.
Even man in the middle captured data, he can't do anything with it because it's encrypted, so it will be useless for him because he can't know what is inside.
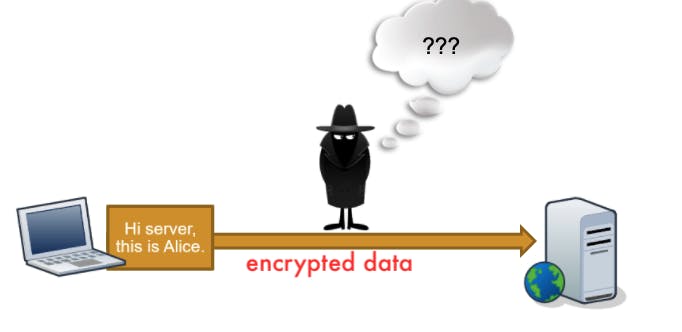
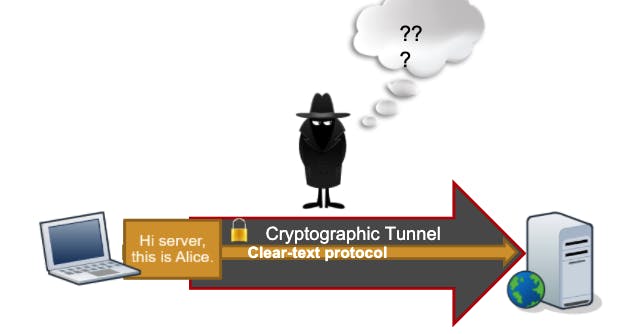
So if you need to transmit private information, you should use cryptographic protocols to protect the communication, over the network, or you can wrap tunnel A clear-test protocol into a cryptographic one Aka: VPN
VPN: Virtual Private networks: use cryptography to extend a private network over a public one, like the internet.
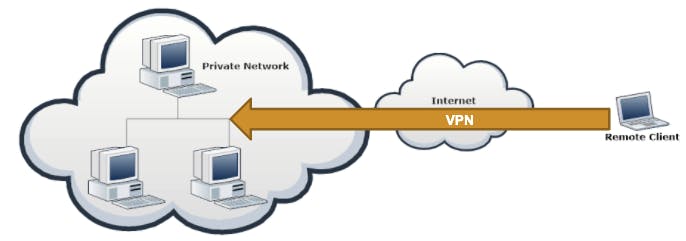
From the client's point of view, being in VPN is the same as being directly connected to the private network.
For Example: when you launch A VPN connection from your Employee area , a Vpn the tunnel is created, letting you connect directly to the office network, giving you an on-premises experience at home.
In the next article, I will write about WireShark, HTTPS and traffic sniffing, So stay tuned
References :
Ine.com platform, Captain Crunch Wikipedia.com, The conscience of a hacker,
Written by : Mohamed Abdalla Ibrahim
PMP | CISM | ITIL | CEH | Azure Architect | Azure Security Engineer | IBM Cybersecurity Analyst

