CYBER SECURITY (Penetration Testing Prerequisites) 1.7 TCP and UDP
How Do TCP and UDP support my pentesting career?
it will allow me to perform the TCP session Attacks, advanced DOS attacks, and network scanning
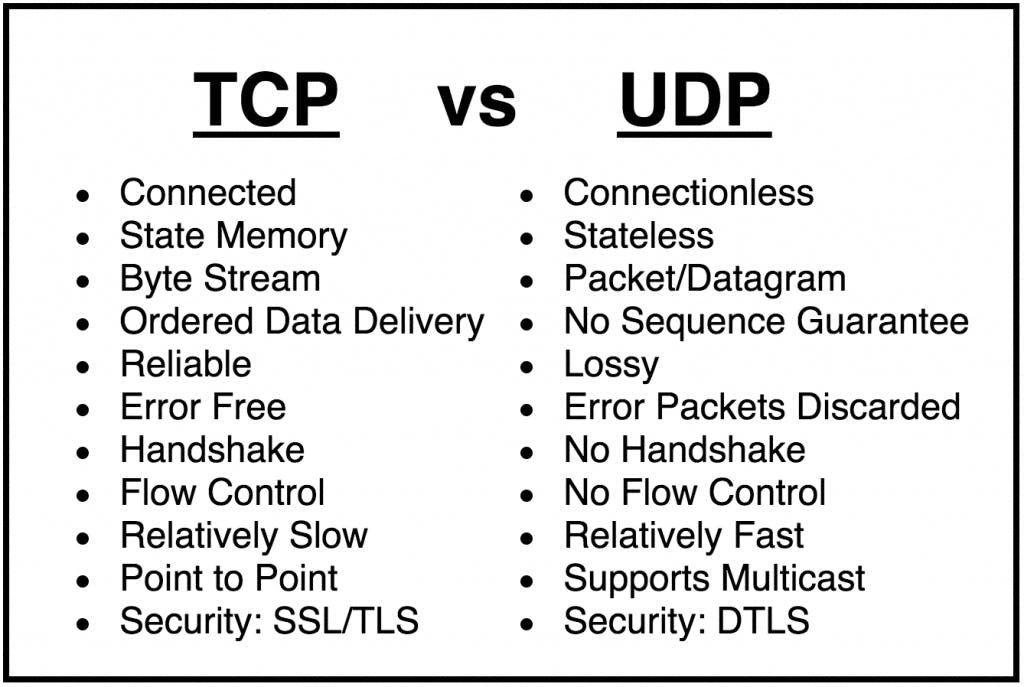
The Transmission control protocol (TCP) and the user datagram protocol (UDP) are the most common transport protocols used on the internet.
before we dive deeper into the different services that the transport layer protocol can offer to the application layer let's consider that, a computer network can be unreliable, this means that some packets can be lost during their tri from the source to the destination, a packet can be lost because of the network congestion, temporary loss of connection and other Technical issues.
when designing a transport layer protocol, the Designer must choose how to deal with these limitations, for example : TCP :
- Grants packet delivery: Because the application needs a guaranteed delivery will use TCP as the transport protocol.
also connection-oriented, it must establish a connection before transferring data.
keep in mind these facts.
TCP is the most transported protocol on the internet, the vast majority of applications use it, and the IP protocol suite is often called TCP/IP.

- On the other hand, UDP is much more simple than TCP :
- it doesn't guarantee packet delivery and its connectionless.
-> UPD is faster than TCP, as it provides better throughput, it is used by multimedia applications that can tolerate packet loss.
Ex: UDP is used for VOIP and video streaming.
PORTS
Applications and their processes use TCP and UDP to send and receive data over the network, when an IP datagram reaches a host, how can the transport layers know what the destination process is? -> here ports role come
ports are used to identify a single network process on a machine
-> let me explain it more in the following example :
assume that we have a PC that uses different ports :
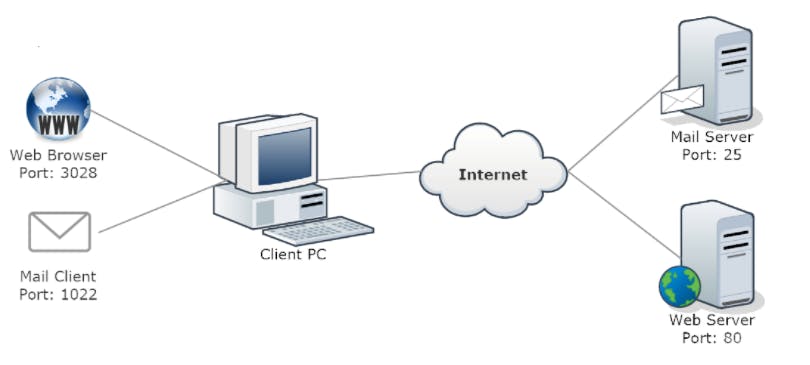
- the browser uses local port 3028 to connect to the webserver.
- While the mail client uses local port 1022.
- all communication from the web browser to the web server will have 3028 as the source port and 80 as the destination port.
- all the communication back from the webserver to the browser will have 80 as the source port and 3028 as the destination port.
Well-known ports
- Each common protocol has a well know ports in the 1023 range, common server process or daemons, well-known ports most of the time.
- ports are assigned by IANA and referenced in this link
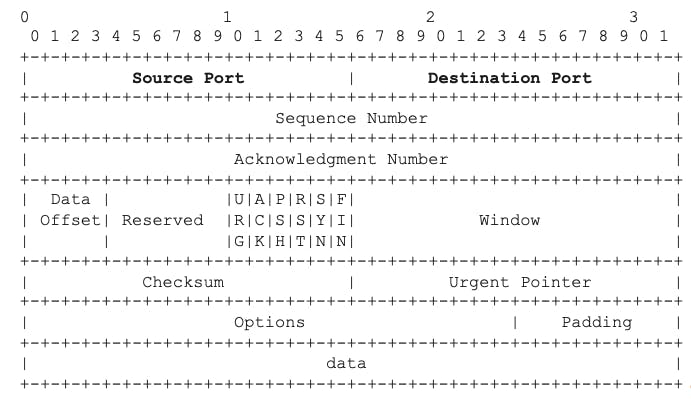
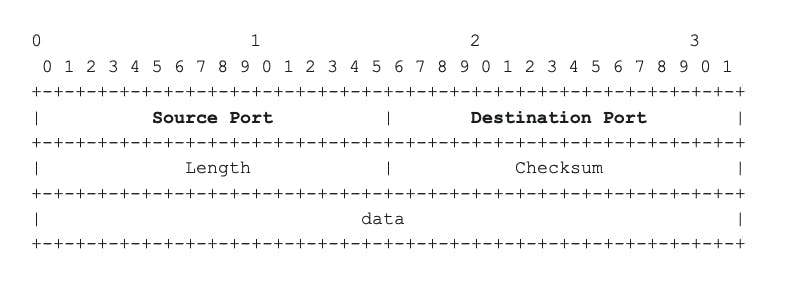
TCP and UDP Headers
How can server and client applications know which port to use : they use two fields in the TCP or UDP header: the source and destination ports :
TCP Header :
UDP Header :
In the next article, I will write about Firewall and Network Defense.
Written by : Mohamed Abdalla Ibrahim
PMP | CISM | ITIL | CEH | Azure Architect | Azure Security Engineer | IBM Cybersecurity Analyst###