While You work as a security analyst and want to know the capabilities of Microsoft 365 Defender to see how it can reduce the time between attack detection and its remediation. Your organization also uses other Microsoft security products and you want to understand what they are and how they fit with Microsoft 365 Defender.
What is Microsoft 365 Defender?
-> Microsoft 365 Defender is a unified enterprise defense solution that automatically aggregates and analyzes signal data from multiple sources, for example, anomalous behavior from Microsoft Defender for Endpoint or a suspicious login from Microsoft Defender for Identity. It then correlates the data into an incident that represents an attack and provides easy investigation and response across endpoints, identities, email, and applications
Microsoft 365 Defender features:
- Unified Cross-product view
- Combined incidents queue
- Self-healing for compromised devices, user identities, and mailboxes Cross-product threat hunting
- Threat Analytics
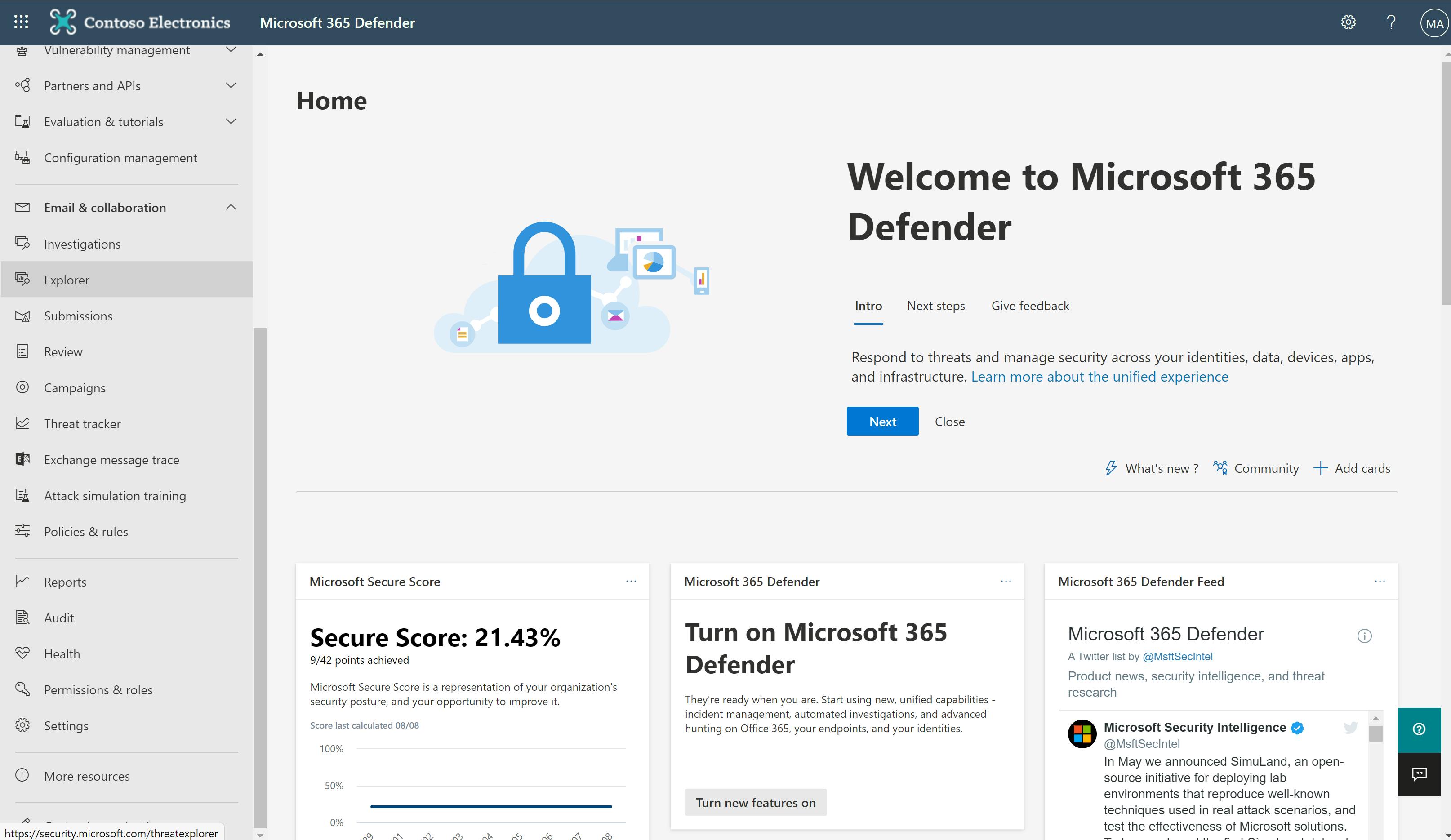
The Microsoft 365 Defender portal :
The Microsoft 365 Defender portal provides access to:
- Incidents: See the broader story of an attack through the aggregation and analysis of alerts and other threat signals.
- Alerts: See the list of specific alerts across your Microsoft 365 environment and dive into the details for your users, emails, or devices.
- Advanced hunting: Search for malware, suspicious files, and activities across your Microsoft 365 organization as part of an incident analysis or proactively for ongoing scanning of cyber threats.
- Threat Analytics: Get a summary view and details on active threats in the cybersecurity community.
- Secure score: Get an all-up summary and calculated score of the different security features and capabilities you've enabled, including recommendations for areas to improve your score.
- Learning hub: Browse through Microsoft 365 security learning paths to quickly ramp up on Microsoft 365 Defender security products.
- Reports: View the information needed to better protect your organization, identities, devices, apps, and infrastructure.
-> Before you started you'll first need to verify that you have the right licenses and permissions to access the portal.
You have to check the licenses, for example, Microsoft Defender for Endpoint, Microsoft Defender for Office 365, or Microsoft Defender for Identity. These services increase your visibility of threat signals from assets across your network.
-> To enable Microsoft 365 Defender, you must be a global administrator or a security administrator in your organization's Azure Active Directory (Azure AD).
and also you should be noted that The supported security services are:
Microsoft Defender for Endpoint: Endpoint protection suite built around powerful behavioral sensors, cloud analytics, and threat intelligence.
Microsoft Defender for Office 365: Advanced protection for your apps and data in Office 365, including email and other collaboration tools like Microsoft Teams.
Microsoft Defender for Identity: Defend against advanced threats, compromised identities, and malicious insiders.
Microsoft Defender for Cloud Apps: Identify and combat cyber threats across your Microsoft and third-party cloud services.
Manage access to Microsoft 365 Defender
There are two ways to manage access to Microsoft 365 Defender. The first is to use the Global Azure AD roles, and the second is by using custom roles.
Permissions and roles
To manage access to Microsoft 365 Defender, you'll need to assign permissions and roles to your security team members. Permissions and roles are managed in the Microsoft 365 Defender portal.
Sign in to the Microsoft 365 Defender portal at .
In the navigation pane, select Permissions & roles.
On the Permissions & Roles page, select Roles.
--> From here, you can give the required roles to your users.
Classifying incidents and alerts
It's important to make sure that you correctly identify and classify active or resolved incidents and alerts as either true or false. Doing this helps tune the detection system so that it can correctly flag genuine attacks. Classifying incidents helps:
- Share knowledge based on the history of similar items.
- Microsoft 365 Defender tune detection and classifications with data from all Microsoft customers.
- Track trends to improve incident evaluation quality.
To know more about classifying incidents please check this link
You Also Can Use email notifications in Microsoft 365 Defender
Microsoft 365 Defender, when it creates a new incident or if there's an update on an existing incident, can send an email notification to you or your security team. This email contains:
- The incident name
- The severity level
The category of incident
You can create files for incidents notifications : to start receiving notifications for new incidents and their progress you can find out the steps by following this link
Written by : Mohamed Abdalla Ibrahim
PMP | CISM | ITIL | CEH | Azure Architect | Azure Security Engineer | IBM Cybersecurity Analyst

