Protocols are used in every computer network communication and you need to know how they work and how to exploit them.
In a computer network, machines talk to each other by means of protocols, ensuing the different hardware and software can communicate, there is a large variety of networking protocol each one has its own purpose, I will write about a few of them, just proof of concept.
Thy primary goal of networking is to exchange information between network computers, that information is carried by packets. Packets are streams of bits running as electric signals on physical media used for transmitting data, such as wired or wireless. As we know these electric signals are (Zeros and Ones) that can represent information.
Every packet has the following structure :
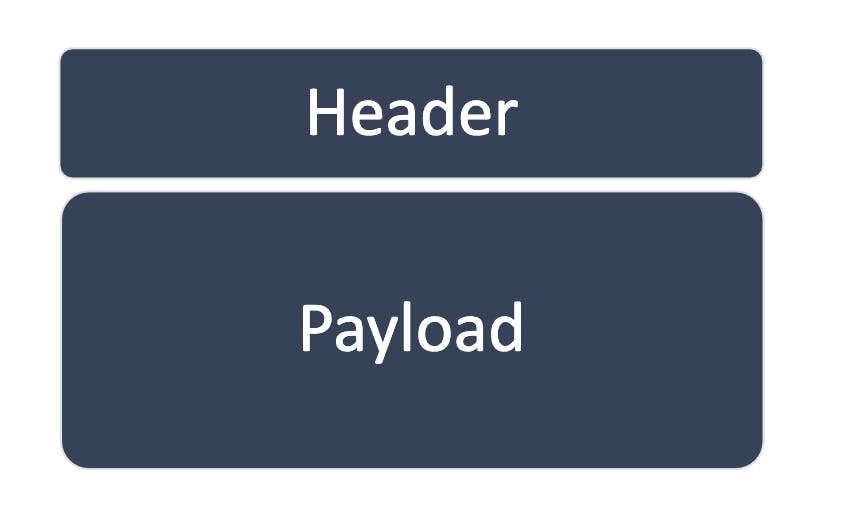
The Header: has a protocol-specific structure: which ensures that the receiving host correctly interprets the payload and the overall communication. The Payload: is the actual information aka (part of an email message, the content of file while downloading, part of the picture, and so on ).
Let Me explain it with an areal example:
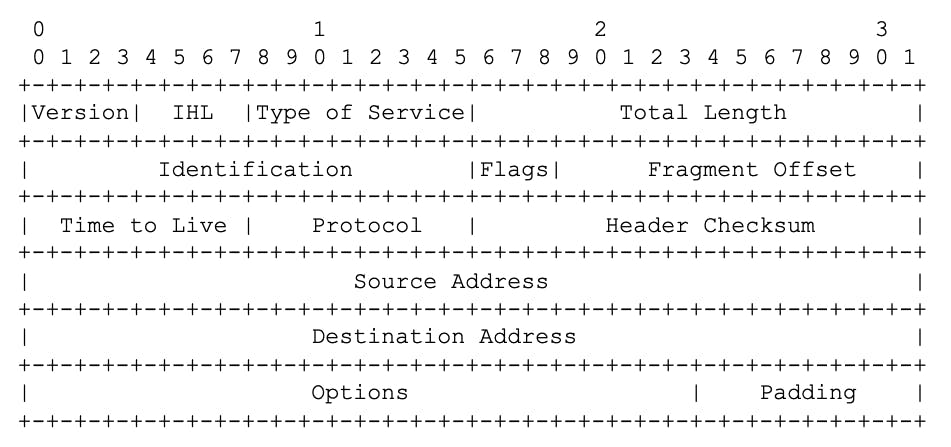
- The IP protocol header is at least 160 bits (20 bytes) long
- The 1st four bits identify the IP Version (Version) which can be IP4 or IP6
- The 32 Bits starting at poison 96 represented the source address and destination address.
Protocol Layers: The previous examples show the header of IP address there are many protocols out there, each one has a specific purpose such as exchanging email, file transfer, VOIP calls, establishing communication between server and client, identifying a computer on the network, transmitting data, and so on.
Moreover, we can say that every layer in the network has its own protocols.
- Application Layer
- Transport layer
- Network layer
- Physical Layer
This will lead us to mention ISO/OSI model :
International Organization standardization (ISO) published a theoretical model for network system communication: the Open System Interconnection (OSI) Model

let us assume that your mother tongue language is french and you have a colleague whose mother tongue is Japanese, you can't speak Japanese and He/She can't speak french, working in the same company, so the company must identify in the regulation the communication default language aka English. to facilitate communication and avoid conflicts inside the company. For that reason, ISO created the OSI model, to unit the communication language.
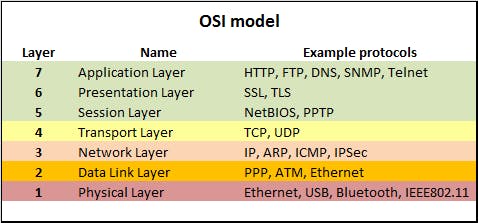
This figure shows the seven layers and some protocols working and each layer. you can find more about OSI Model here
In the next article, I will write about Encapsulation.
Written by : Mohamed Abdalla Ibrahim
PMP | CISM | ITIL | CEH | Azure Architect | Azure Security Engineer | IBM Cybersecurity Analyst