CYBER SECURITY (Penetration Testing Prerequisites) 1.6 Link-layer Devices and protocols
In that article, we will dive into link layers devices and protocols, but before we start we have to know how does this support my career as a pentester :
- MAC spoofing
- Testing Switches security
- sniffing techniques
- man in the middle attack
And if you are not familiar with any of them don't worry I will explain each point in detail in the next few articles so, stay tuned
Packet forwarding also happens in the lowest layer of the TCP/IP stack: the link-layer.
While routers are aware of the best overall path destination, next layer devices and protocols deal only with the next hop
Okay, let us start and see the following :
- How switches work
- Network cards MAC Addresses
- The address resolution protocol (ARP)

Link layers Devices :
Hub And Switches are network devices that forward frames "layer 2 Packet" on the local network, they work with MAC addresses.
MAC Addresses (Physical addressed): Are uniquely identify a network card while IP addresses are addressing schemes used to identify y the host on the network.
To discover the MAC address of the network cards installed on your computer, you can use the following commands :
ipconfig /all
on windows
ifconfig
on nix OS like macOS
IP addr
on linux
One point you should always remember the lower layers serve the above layers.
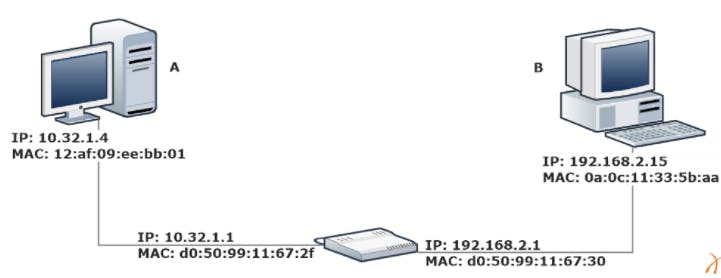
This figure can be an example to show how MAC address is used and how it works :
Two different networks are connected together by a router. Every machine on the network has both IP and mac address and the router have two interfaces each with its own addresses. Host A won't send the package to host B So Host A will create a package with :
- The Destination IP address of host B in the IP Header
- The destination ma address of the router
- The source IP address of workstation A
- The Source MAC address of work station A
Then the router will take the package and forward it to the C network rewriting the packet mac address :
- The destination mac will be C
- And the source mac will be the router
- Your router will not change the source and destination IP addresses
Switches
While routers work with IP addresses, switches work with MAC addresses. Switches also have multiple interfaces, so they need to keep a forwarding table that binds one or more MAC addresses to an interface.
Ex:
-The main difference between one switch and another is the packet forwarding speed.
-The speed of a switch varies from 10Mbps (megabits per second) to 10Gbps (gigabits per second). Nowadays, 1Gbps is the most common forwarding speed in commercial switches.
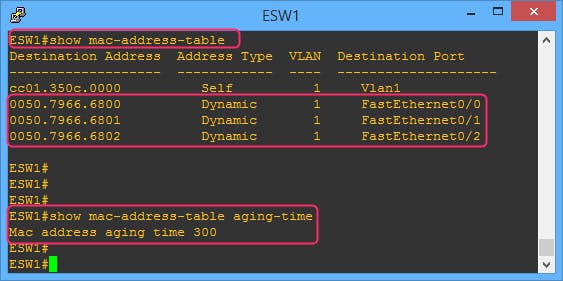
CAM Table Population
Switches learn new MAC addresses dynamically; they inspect the header of every packet they receive, thus identifying new hosts.
While routers use complex routing protocols to update their routing rules, switches just use the source MAC address of the packets they process to decide which interface to use when forwarding a packet.
The source MAC address is compared to the CAM table:
If the MAC address is not in the table, the switch will add a new MAC-Interface binding to the table
If the MAC-Interface binding is already in the table, its TTL gets updated
If the MAC is in the table but bound to another interface the switch updates the table
Forwarding
To forward a packet:
1-The switch reads the destination MAC address of the frame.
2-It performs a look-up in the CAM table.
3-It forwards the packet to the corresponding interface.
4-If there is no entry with that MAC address, the switch will forward the frame to all its interfaces.
ARP
This situation occurs in many circumstances, for example at every power-up. -A PC in an office knows a bunch of IP addresses, like the fileserver, the printers, and the web server, but not their corresponding MAC addresses.
-The host needs to know the MAC addresses of the other network nodes and it can learn them by using the Address Resolution Protocol (ARP).
-With ARP a host can build the correct IP Address - MACaddress binding.
-This is one of the most fundamental protocols any modern the network uses, so make sure to fully understand it.
In the next article, I will write about TCP and UDP.
Written by : Mohamed Abdalla Ibrahim
PMP | CISM | ITIL | CEH | Azure Architect | Azure Security Engineer | IBM Cybersecurity Analyst